Sept
2014
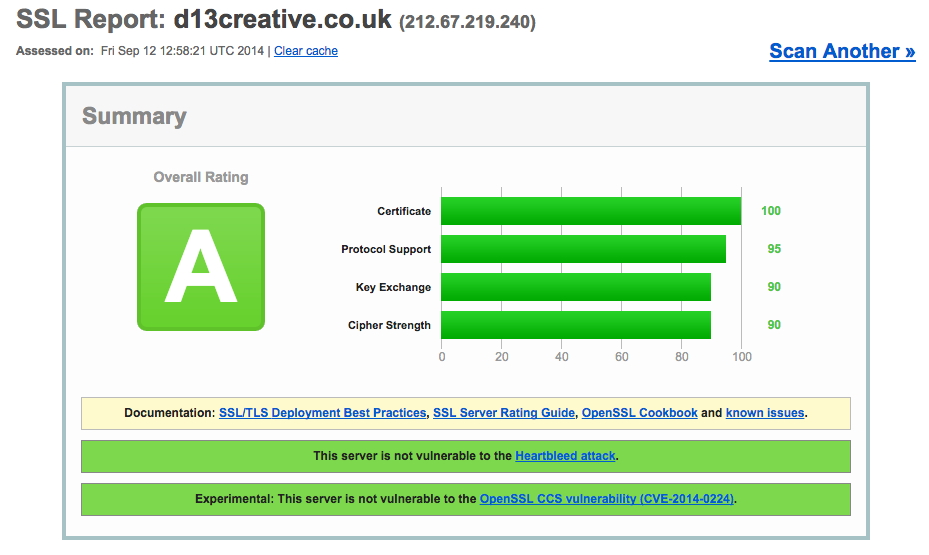
I already had SSL enabled on my linux server but according to tests it was using TLS level 1.0, not the more secure 1.2 and hence I only scored a B in the test. Here's a brief guide to how I enabled TLS 1.2 on my server and improved the grade to an A. Please note some of these steps will be specific to my server setup so they may not work for you. I will assume a basic knowledge of the terminal.
First of all I navigated to /etc/nginx/ and ran the following command:
# openssl dhparam -out dhparam.pem 4096
I was warned it would take a long time but as it turned out it was only a few minutes although I have heard on slower servers it could take several hours. I then created new folders for my custom .conf files which are required for the TLS settings and copied the default files into the respective folders:
# mkdir -p /usr/local/psa/admin/conf/templates/custom/domain # mkdir -p /usr/local/psa/admin/conf/templates/custom/server # cp /usr/local/psa/admin/conf/templates/default/nginxWebmailPartial.php /usr/local/psa/admin/conf/templates/custom/ # cp /usr/local/psa/admin/conf/templates/default/domain/nginxDomainVirtualHost.php /usr/local/psa/admin/conf/templates/custom/domain/ # cp /usr/local/psa/admin/conf/templates/default/server/nginxVhosts.php /usr/local/psa/admin/conf/templates/custom/server/
Next step was to modify the three files which have just been copied to the custom folders, nginxWebmailPartial.php, nginxDomainVirtualHost.php and nginxVhosts.php. The following lines
ssl_protocols SSLv2 SSLv3 TLSv1; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on;
Were replaced with
ssl_session_cache shared:SSL:50m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA; ssl_prefer_server_ciphers on; ssl_dhparam /etc/nginx/dhparam.pem;
*** a note of caution on the ciphers used above: I have used the ciphers for intermediate compatibility as found on Mozilla's website. Your needs for compatibility may be different so choose the cipher appropriate to your needs. Also security requirements are constantly changing so you will need to review them periodically ***
Finally the following commands were run to reconfigure and reload nginx:
# /usr/local/psa/admin/bin/httpdmng --reconfigure-all # nginx -s reload
Hey presto, TLS 1.2 is now running correctly! I followed various bits of advice from the web to get to this point some of which worked for some people but not for me without some modification. For example, the ciphers I'd originally used from Qualsys contained quotes and were not delimited by colons but I was helped out at the Parallels' forum.
Hope this helps!